1 Security Concepts of Information Assurance
This chapter introduces foundational cybersecurity concepts through the lens of information assurance, framing organizations as socio-technical systems where people, processes, and technology interact to create value. It emphasizes that infrastructure spans both physical and digital domains and that information systems—whether pre- or post-digital—bind these elements together for decision making. With cloud and hybrid environments redefining where and how work happens, the central mission of cybersecurity engineers is to understand the organization, the risks it faces, and to implement effective controls that keep operations resilient against disruptive events.
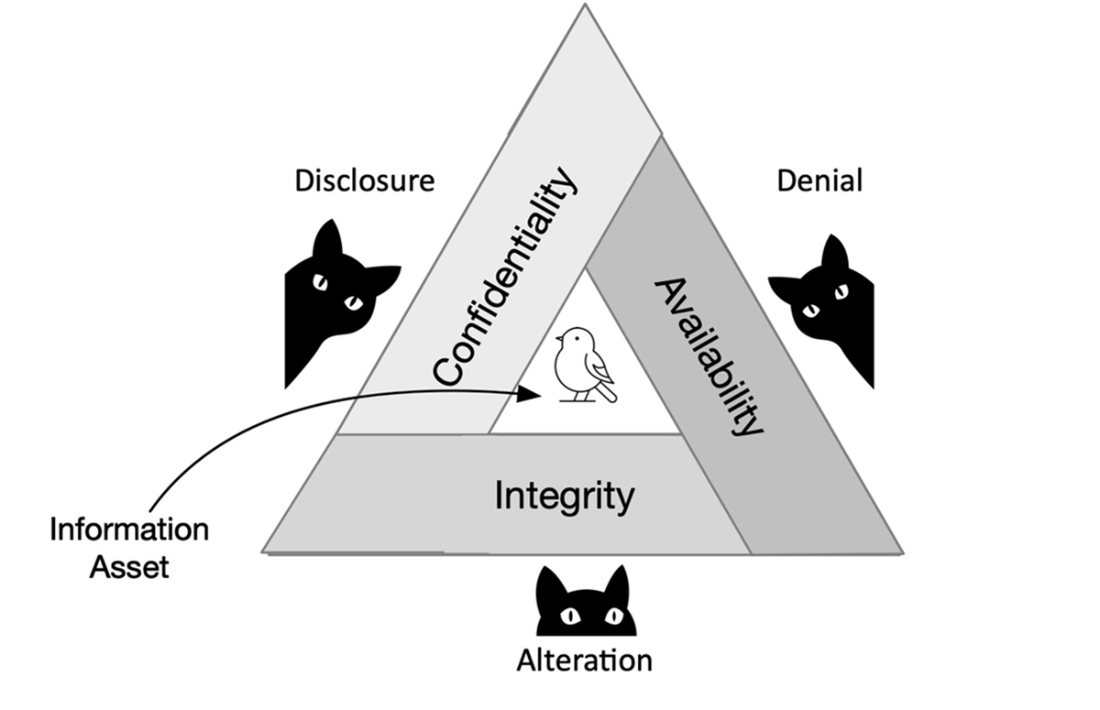
Assets are categorized as tangible, intangible, and human, with data and information systems often among the most valuable and sensitive. The text clarifies the relationships between vulnerabilities (weaknesses), threats (potential sources of harm, whether accidental or malicious), and attacks (intentional exploitation), and profiles a spectrum of threat actors from insiders and script kiddies to criminal syndicates and nation-state–backed APTs. It outlines security controls—physical, technical, and administrative—that work together to reduce risk, and anchors protection objectives in the CIA triad: confidentiality, integrity, and availability. The chapter also pairs these principles with the DAD perspective—disclosure, alteration, and denial—and maps appropriate safeguards such as encryption and access control for confidentiality, hashing and digital signatures for integrity, and redundancy, failover, and backups for availability.
Because not all information carries the same impact if exposed or altered, the chapter promotes data classification to guide handling, storage, access, and protection. It distinguishes sensitive from confidential information, describes common classification tiers (e.g., public, internal, confidential, highly confidential), and explains how classification prioritizes control implementation. It further details key data categories including PII—separating non-public personal information from public personal information—and PHI, noting their heightened sensitivity and the need for privacy-preserving measures. Mastery of these concepts underpins information assurance and provides the practical foundation for applying risk-based controls to protect organizational assets in real-world scenarios.
Illustration of the interdependence of the key information security principles of confidentiality, integrity, and availability along with the corresponding threats of disclosure, alteration, and denial.
Answers to Review Questions
- The correct answer is D. Software is not a tangible asset. Unlike hardware, buildings, and machines, which have a physical form and can be touched, software is intangible. It consists of code and data that exist digitally rather than physically.
- The correct answer is C. Availability is the component of the CIA triad that focuses on ensuring that information is available when it is needed. On the other hand, while Confidentiality and Integrity are part of the CIA, they have different purposes. Authentication is not part of the CIA triad.
- The correct answer is A. Any factor that has the potential to disrupt an asset by exploiting a vulnerability is known as a threat. Threats can take many forms, including malicious actors such as hackers, computer viruses, or natural disasters such as hurricanes or earthquakes. The remaining options, on the other hand, are not threats because the first two unchecked options represent vulnerabilities, and the last unchecked option emphasizes the need for protective measures on an asset to counter potential threats.
- The correct answer is C. A threat actor is an individual or entity responsible for launching cyberattacks. The remaining options are incorrect because a software vulnerability is a vulnerability, a phishing email is a threat vector, and a denial-of-service attack is an example of an attack method.
- The correct answer is C. PII (Personally Identifiable Information) includes personal information such as names and addresses, while PHI (Protected Health Information) is a subset that focuses on health information, including medical records and treatment details. PII and PHI must be protected, but PHI has additional regulatory requirements.
FAQ
What is Information Assurance and how does it relate to the CIA Triad?
Information Assurance is the practice of protecting information and information systems against threats that could compromise their confidentiality, integrity, and availability (the CIA Triad). It guides risk-based decisions and the selection of controls to keep data accurate, private, and accessible when needed.What counts as an asset in cybersecurity, and how do tangible, intangible, and human assets differ?
An asset is anything of value to an organization that requires protection. Tangible assets are physical (e.g., buildings, servers, network gear). Intangible assets are non-physical (e.g., data, software, patents, brand reputation). Human assets include employees, contractors, and vendors. Each category needs tailored protections (physical, technical, legal/administrative, and training).How has cloud computing changed the concept of organizational infrastructure?
Cloud computing shifts infrastructure from on-premises to provider-managed services or hybrid models. “The office” is no longer tied to one location (remote work, co-working, third-party datacenters). Security must account for shared responsibility with cloud providers, distributed assets, and securing access from anywhere.What is the difference between a vulnerability, a threat, an attack, and a threat actor?
- Vulnerability: A weakness in an asset (e.g., misconfiguration, software bug, poor process) that can be exploited.- Threat: Any potential cause of harm that can exploit a vulnerability (malicious or non-malicious).
- Attack: The intentional exploitation of a vulnerability.
- Threat actor: The person or group conducting an attack (e.g., insider, cybercriminal).
Who are common threat actors and what motivates them?
Common threat actors include insiders (employees/contractors), script kiddies (inexperienced attackers using ready-made tools), thrill seekers (challenge/fun), hacktivists (political/social motives), criminal syndicates (profit), and advanced persistent threats/APTs (often state-sponsored, highly resourced). Motivations range from curiosity to ideology, profit, and espionage.What types of security controls exist and what do they protect?
- Physical controls: Guard access to facilities and hardware (locks, cameras, badges).- Technical controls: Protect systems and data (firewalls, encryption, anti-malware, access control).
- Administrative controls: Policies, procedures, and training that guide secure behavior. Controls often overlap and are layered to reduce risk.
What is the CIA Triad and why is it foundational?
The CIA Triad comprises confidentiality (only authorized access), integrity (data is accurate and unaltered except by authorized means), and availability (systems and data are accessible when needed). It defines the core properties to protect and anchors how we identify risks and choose controls.What is the DAD Triad and how does it complement the CIA model?
The DAD Triad maps the main threat classes to CIA: Disclosure (breaks confidentiality), Alteration (breaks integrity), and Denial (breaks availability). Thinking in DAD helps anticipate how attacks manifest (e.g., eavesdropping, tampering, DoS) and what safeguards are needed.What is data classification and what levels are commonly used?
Data classification organizes information by sensitivity and business impact to apply appropriate protections. Common levels include Public, Internal, Confidential, and Highly Confidential/Restricted. Higher sensitivity demands stricter handling, storage, access, and protection requirements.How do sensitive, confidential, PII, and PHI differ?
- Sensitive: Any data that could harm an individual or organization if mishandled.- Confidential: Sensitive data that must be intentionally restricted (often with legal/contractual obligations).
- PII: Data that identifies a person. Includes Non-Public Personal Information (e.g., SSN, bank details) and Public Personal Information (e.g., public job title) that can identify when combined.
- PHI: Health-related data tied to an individual (e.g., medical records, insurance info) requiring stringent privacy controls.
 Acing the ISC2 Cybersecurity Certification Exam ebook for free
Acing the ISC2 Cybersecurity Certification Exam ebook for free