1 Security Concepts of Information Assurance
This chapter introduces the foundations of information assurance by framing organizations as socio-technical systems where people, processes, and technology create value. Cybersecurity’s role is to keep those systems resilient by understanding organizational context, identifying relevant threats, and applying effective controls to mitigate risk. The chapter sets the stage with core terminology and models—especially the confidentiality, integrity, and availability (CIA) triad—that guide how professionals think about protecting information systems and the assets they enable.
Key concepts are defined with an emphasis on what must be protected and from whom. Assets span tangible (facilities, equipment, networks), intangible (data, software, intellectual property, brand), and human resources, all of which can have vulnerabilities stemming from flaws, misconfigurations, weak practices, or human error. Threats may be non-malicious (failures, accidents, natural events) or malicious (intentional attacks), and an attack is the deliberate exploitation of a vulnerability by a threat actor. Threat actors range from insiders and novice “script kiddies” to hacktivists, criminal syndicates, and well-resourced nation-state groups. To counter these risks, organizations deploy physical, technical, and administrative controls—often in combination—selected through a risk-based approach.
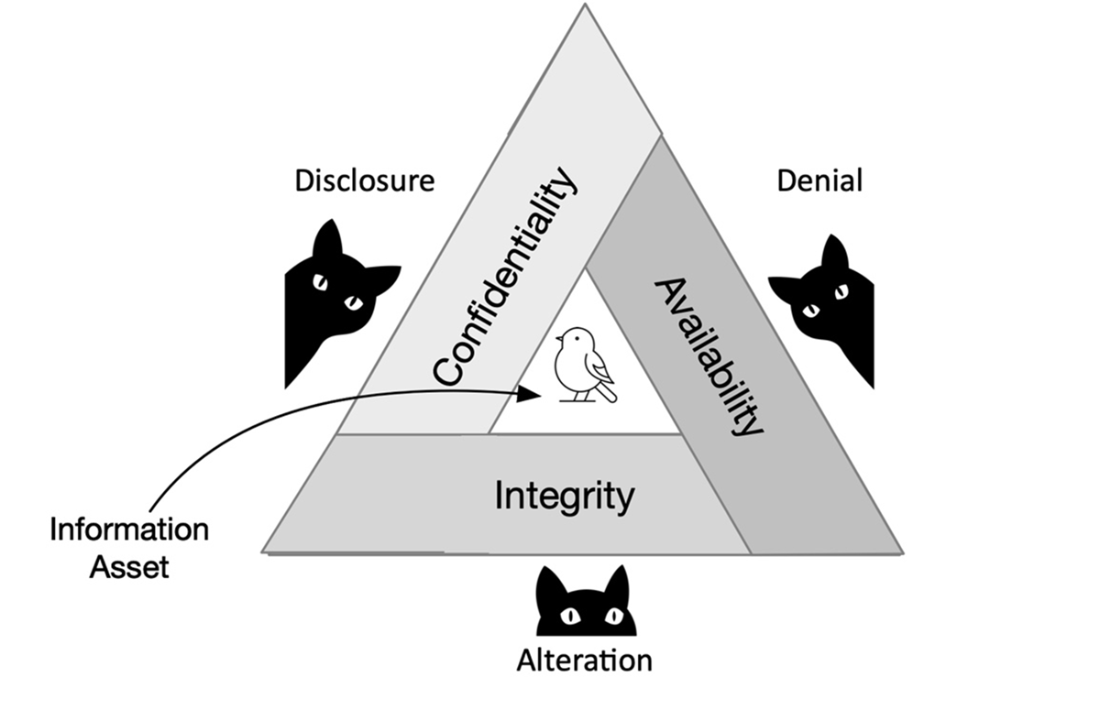
The CIA triad structures protection goals: confidentiality (preventing unauthorized access), integrity (preventing unauthorized alteration), and availability (ensuring timely access), with typical safeguards such as encryption and access control for confidentiality, hashing and digital signatures for integrity, and redundancy and backups for availability. The complementary DAD view (Disclosure, Alteration, Denial) helps map threat classes to protections. Because not all information has equal value, the chapter closes with data classification—labeling information by sensitivity (e.g., public, internal, confidential, highly confidential) to drive handling requirements—and clarifies categories like sensitive vs. confidential data, personally identifiable information (PII, including public and non-public forms), and protected health information (PHI). Together, these concepts establish the baseline practitioners use to prioritize controls and defend real-world environments.
Illustration of the interdependence of the key information security principles of confidentiality, integrity, and availability along with the corresponding threats of disclosure, alteration, and denial.
Answers to Review Questions
- The correct answer is D. Software is not a tangible asset. Unlike hardware, buildings, and machines, which have a physical form and can be touched, software is intangible. It consists of code and data that exist digitally rather than physically.
- The correct answer is C. Availability is the component of the CIA triad that focuses on ensuring that information is available when it is needed. On the other hand, while Confidentiality and Integrity are part of the CIA, they have different purposes. Authentication is not part of the CIA triad.
- The correct answer is A. Any factor that has the potential to disrupt an asset by exploiting a vulnerability is known as a threat. Threats can take many forms, including malicious actors such as hackers, computer viruses, or natural disasters such as hurricanes or earthquakes. The remaining options, on the other hand, are not threats because the first two unchecked options represent vulnerabilities, and the last unchecked option emphasizes the need for protective measures on an asset to counter potential threats.
- The correct answer is C. A threat actor is an individual or entity responsible for launching cyberattacks. The remaining options are incorrect because a software vulnerability is a vulnerability, a phishing email is a threat vector, and a denial-of-service attack is an example of an attack method.
- The correct answer is C. PII (Personally Identifiable Information) includes personal information such as names and addresses, while PHI (Protected Health Information) is a subset that focuses on health information, including medical records and treatment details. PII and PHI must be protected, but PHI has additional regulatory requirements.
FAQ
How do people, processes, and technology interact within an organization?
People, processes, and technology (infrastructure) form a socio-technical system that creates value. Physical infrastructure (buildings, servers, networks) and digital infrastructure (software, data) support business processes, which are executed by people. Cybersecurity aims to keep these components operating without disruption from threats.What is an asset in cybersecurity, and what types of assets exist?
An asset is anything of value to the organization that requires protection. Common categories: tangible (e.g., buildings, servers, network equipment), intangible (e.g., data, software, intellectual property, brand reputation), and human assets (employees, vendors/contractors). Different asset types require different safeguards.What are vulnerabilities, threats, attacks, and threat actors?
- Vulnerability: a weakness in an asset (e.g., software bug, misconfiguration, poor practices).- Threat: any factor that could exploit a vulnerability and cause harm (malicious or non-malicious like natural disasters).
- Attack: the intentional exploitation of a vulnerability.
- Threat actor: the person/group conducting an attack (e.g., insider, cybercriminal, APT).
What is Information Assurance and how does it relate to the CIA Triad?
Information Assurance is the activity of protecting information and information systems from threats that could compromise their confidentiality, integrity, and availability (CIA).- Confidentiality: only authorized access to information.
- Integrity: information remains accurate and unaltered (except by authorized means).
- Availability: information and systems are accessible when needed.
What is the DAD Triad and how does it map to the CIA Triad?
The DAD Triad describes threat classes that oppose CIA:- Disclosure → compromises Confidentiality (e.g., eavesdropping on emails).
- Alteration → compromises Integrity (e.g., unauthorized database changes).
- Denial → compromises Availability (e.g., DoS attacks). Thinking in DAD helps select controls to preserve CIA.
Who are common threat actors and what characterizes them?
- Insider threats: employees/contractors misusing access (e.g., data leaks).- Script kiddies: low-skill actors using ready-made tools.
- Thrill seekers: motivated by challenge/fun.
- Hacktivists: driven by political/social causes.
- Criminal syndicates: profit-motivated groups (e.g., ransomware).
- APTs: highly resourced, often nation-state–sponsored, long-term campaigns.
What types of security controls protect assets?
- Physical controls: locks, guards, cameras, access cards.- Technical controls: firewalls, encryption, authentication/authorization, antivirus.
- Administrative controls: policies, procedures, training, awareness.
Controls often overlap; selecting the right mix is risk-based and may protect multiple assets simultaneously.
What is data classification and what levels are commonly used?
Data classification organizes information by sensitivity/impact to guide handling and protection. Common levels:- Public: safe to share (e.g., marketing materials).
- Internal: for internal use only (e.g., policies, internal comms).
- Confidential: could harm org/customers if disclosed (e.g., contracts, customer data).
- Highly Confidential: severe impact or legal risk if exposed (e.g., trade secrets, PII, health records).
What is the difference between sensitive and confidential information?
Sensitive information can cause harm if improperly accessed or disclosed (e.g., personal interests, internal financials). Confidential information is sensitive data that must be intentionally restricted to authorized parties, often with formal/legal obligations (e.g., medical records, trade secrets). Not all sensitive data is confidential (e.g., a birthdate may be sensitive but sometimes publicly shared).What are PII and PHI, and how do they differ?
- PII (Personally Identifiable Information): attributes that identify an individual. Includes Non-Public Personal Information (e.g., SSN, bank details, non-public email/phone) and Public Personal Information (e.g., job title, public directory listings). Less obvious identifiers include IP addresses, usernames, browsing history, photos, and audio.- PHI (Protected Health Information): health-related data (e.g., medical records, insurance info, lab results) that is especially sensitive and typically requires strict privacy controls (e.g., anonymization).
 Become ISC2 Certified in Cybersecurity ebook for free
Become ISC2 Certified in Cybersecurity ebook for free