1 Making Sense of Application Security
Modern software operates in a threat-filled world where breaches are frequent, costly, and no longer limited to application code—hardware flaws and vulnerabilities exist at every layer of the stack. Security is a shared responsibility across everyone who builds and runs systems, and its business impact has elevated security leadership and accountability. For developers, this translates into clear expectations: use security features correctly across all products and services, meet corporate standards and audits, design and implement with security in mind, and embrace DevSecOps practices to integrate security throughout delivery pipelines.
Achieving real security requires more than relying on libraries and tools; it depends on understanding the standards, protocols, and patterns those tools implement. Developers often struggle with security frameworks because they lack this foundation, but mastering concepts like TLS and OpenID Connect makes libraries far easier to configure, debug, and apply effectively. The chapter also highlights software supply chain risk: widespread dependency reuse can introduce severe vulnerabilities, making continuous scanning, rapid patching, automated upgrades, and disciplined use of public APIs essential to managing third-party components safely.
Security spans a continuum of roles—from mathematicians and cryptographers to standards authors, implementers, framework builders, corporate security teams, and auditors—each contributing different expertise. Developers don’t need deep mathematical knowledge, but they do need to understand what algorithms and standards do, when to use them, and how to integrate them properly to pass audits and protect users. This book focuses on that practical developer skill set: building a clear mental model of security, applying core cryptography, using common protocols and identity patterns, securing service-to-service communication, avoiding common coding pitfalls, and collaborating effectively with InfoSec to ship trustworthy software.
Headlines showcasing major recent data breaches and security vulnerabilities, emphasizing the widespread impact on millions of users and the persistent threat to digital security.
Layers at the top depend on the layers below them. All the layers are required to produce secure application. The standards, protocols, and patterns used to secure applications are the primary focus of this book, they are the foundation that you need to use security libraries in your application effectively.
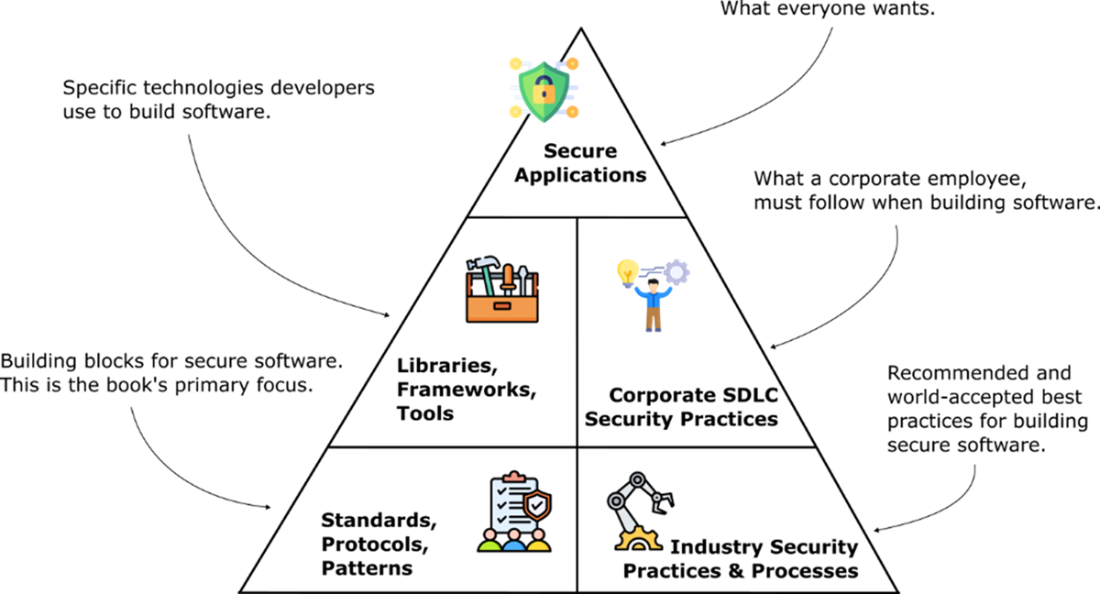
While developers often focus on libraries, frameworks, and tools at the mid-level, true security stems from foundational knowledge of standards, protocols, and patterns, as well as adherence to corporate and industry security practices. Bridging the gap between these layers leads to more effective and secure development.
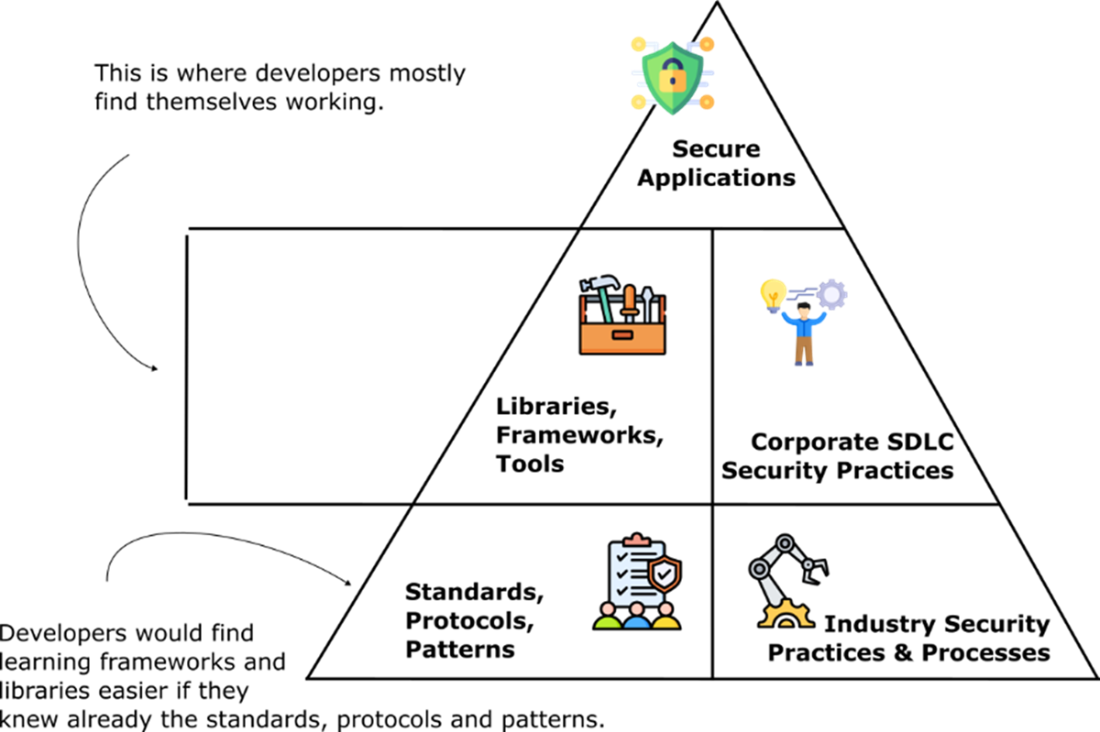
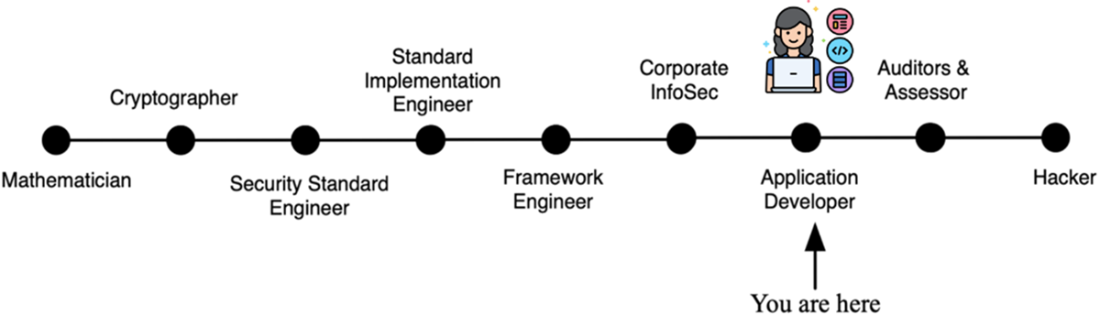
The spectrum of technical roles involved in computer security roles and responsibilities
Summary
- Security vulnerabilities can exist at every layer of the stack, from hardware (e.g., Meltdown, Specter) to application code.
- Security is everyone’s responsibility, not just InfoSec teams - developers play a central role.
- The business impact of breaches is massive (e.g., Marriott, Equifax), often costing millions or even billions.
- CISOs expect developers to:
- Use all product security features
- Follow corporate security standards
- Design and implement secure applications
- Embrace DevSecOps practices
- Security libraries (like Spring Security) are essential but hard to use unless you understand the underlying standards and protocols.
- Supply chain attacks (e.g., Equifax Apache Struts, Event-Stream Bitcoin theft) highlight the need for vigilance in managing dependencies.
- Automated vulnerability scanning in CI/CD pipelines is a best practice to detect and fix issues quickly.
- Stick to published APIs in libraries to ensure maintainability and security over time.
- Different roles contribute to security: mathematicians, cryptographers, standards engineers, framework engineers, InfoSec teams, auditors, and developers.
- Developers don’t need deep expertise in all these roles, but they must understand enough to apply standards and use libraries correctly.
- This book teaches developers the foundations (cryptography, protocols, standards) so they can confidently build secure, reliable applications.
FAQ
Why is application security everyone’s responsibility, not just the security team’s?
Because weaknesses exist at every layer—from CPU hardware to browser JavaScript—anyone who designs, builds, deploys, or operates software can introduce or mitigate risk. Shared responsibility reduces blind spots and raises the baseline across the stack.What are the real business impacts of security breaches?
Breaches routinely cost organizations millions in response, fines, and lost trust. For example, the average breach cost is measured in the millions, some incidents have exposed hundreds of millions of records, and cleanup for high‑profile cases has exceeded a billion dollars. Security can be a company‑ending risk.How do CISO priorities change what developers must do day to day?
Expectations include: using security features in every product you adopt, conforming to corporate standards and passing audits, designing and implementing with security by default, and embracing DevSecOps practices that integrate security into development and operations workflows.Why aren’t security libraries alone sufficient to secure an app?
Libraries enforce mechanics (e.g., TLS handshakes), but overall safety depends on secure design, coding, configuration, and maintenance. Process matters: reviews, static analysis, threat‑aware design, secure defaults, and ongoing patching are essential.Why should developers learn standards, protocols, and patterns (like TLS and OpenID Connect)?
Understanding the foundations makes frameworks easier to configure, reduces trial‑and‑error, speeds up debugging, and helps you justify choices to auditors. With the “why” clear, the “how” in libraries becomes straightforward.What is software supply chain risk, and why is it growing?
Modern apps depend on hundreds of third‑party components. A single vulnerable or malicious dependency can compromise the whole system, as seen in widely publicized incidents. Attackers target supply chains because the blast radius is large and defenses are uneven.How can teams manage and reduce dependency vulnerabilities effectively?
- Use automated scanners to inventory dependencies (direct and transitive) and flag known CVEs- Run scans on every commit; fail builds on high‑risk issues
- Rescan when vulnerability databases update
- Enable automated upgrade PRs and, where safe, auto‑merge with test coverage
- Wire fixes into CI/CD so patches ship quickly
How do we avoid being trapped on outdated, risky libraries?
Code only against public, supported APIs; avoid internal or undocumented interfaces. Maintain regular upgrade cadences, allocate time for refactoring, and keep tests strong so you can adopt new versions confidently.Who does what in security, and where should developers focus?
- Mathematicians and cryptographers create the theory and primitives- Standards engineers define interoperable protocols (e.g., TLS, OIDC)
- Implementers and framework authors build libraries and tooling
- Corporate InfoSec sets policies and advises teams; auditors verify compliance
- Developers should master applying standards via libraries, secure design, and meeting corporate controls.
What core security skills should application developers have?
- Big‑picture understanding of risks and tradeoffs- Cryptography basics (what to use, when, and how to configure)
- Practical use of standards/protocols (TLS, OAuth/OIDC)
- Identity, authentication, and authorization design
- Secure service‑to‑service communication
- Code hygiene: spotting and fixing common flaws
- Supply chain security and tooling (scanners, CI/CD gates)
- Audit readiness and effective collaboration with InfoSec.
 Software Security for Developers ebook for free
Software Security for Developers ebook for free